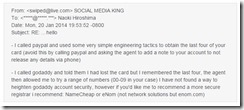
Naoki Hiroshima owned the Twitter account @n, which was in high demand. He would get offers of up to $50,000 for its purchase. It was so in demand that a hacker stole it from him. In a strange twist, Naoki emailed the thief and got the following answer on how the crime was committed.
http://arstechnica.com/security/2014/01/how-i-lost-my-50000-twitter-username/
If you forget your password, Twitter will send your email a reset link. Therefore, if you have access to the email account attached to Twitter, you can reset the email password.
To get access to the email account, you can need to have access to the domain register (i.e. GoDaddy). As you can see from the correspondence above, this was very simple.
If someone can steal your email account, they can reset the password for every account you have. Here are a couple of steps to prevent this from happening.
1. Use a Gmail Address and not your Business’ Address for Important Sites
My email address is Craig.Bayer@optiable.com, however, I never use that to sign up for important websites like investment accounts and domain registers. I use a non-published Gmail account. It might be possible for a hacker to steal my Craig.Bayer@optiable.com account by stealing the optiable.com domain name. A hacker is not going to be able to steal the gmail.com domain account and do the same thing.
Even though they cannot steal the domain name, they could figure out the password via a variety of different methods. That is why I have 2-Factor Authentication on that Gmail account.
2. Turn on 2 Factor Authentication
2-Factor Authentication means that you need to use two forms of identification to log in to a website. The first form is usually your password, and the second form is often a unique password that is texted to your mobile device.
You can turn on two Factor Authentication for sites like:
· DropBox
· GoDaddy
· Microsoft 365
· Gmail
· Online Banking
Now, if someone wants to hack my email and have acquired my password, they must also be in possession of my mobile phone.